A total of 16 people with ties to the “hacktivist” group “Anonymous” were arrested by the FBI on Monday. Fourteen of them were charged in connection with an attack on PayPal, which was targeted by “Anonymous” because the website suspended the account of WikiLeaks after it released classified State Department cables.
An affidavit from an FBI special agent reveals how the bureau tracked down 21-year-old Arciszewski of Florida, who is accused of attacking the Tampa Bay Infraguard website. First, they got the IP address of the individual who attacked the website with the account “AntiSecTest” on June 21. Then they used info on the Twitter account voodooKobra which posted a “bitly” link to the vulnerability he allegedly created with the phrase “Infraguard Tampa has one hell of an exploit.”
Based on the twitter info associated with the Twitter account, they visited his website at kobrascorner.com and did a Google search for his “VoodoKobra” screenname. They turned up his Wikipedia user page, which listed his real name as Scott Arciszewski. They compared his drivers license photo to the avatar on his account on hackforums.net and on his Facebook profile.
From TalkingPointsMemo: http://idealab.talkingpointsmemo.com/2011/07/fbi-arrests-college-students-cashiers-and-a-landscaper-for-anonymous-hacks.php
Pictures of the hackers themselves: http://media.talkingpointsmemo.com/slideshow/anonymous-mugshots-unmasked/1-213620


 The governments of the United States, Canada, and South Korea, as well as the UN, the International Olympic Committee, and 12 US defense contractors were among those hacked in a five-year hacking campaign dubbed “Operation Shady RAT” by security firm McAfee, which revealed the attacks. Many of the penetrations were long-term, with 19 intrusions lasting more than a year, and five lasting more than two. Targets were found in 14 different countries, across North America, Europe, India, and East Asia.
The governments of the United States, Canada, and South Korea, as well as the UN, the International Olympic Committee, and 12 US defense contractors were among those hacked in a five-year hacking campaign dubbed “Operation Shady RAT” by security firm McAfee, which revealed the attacks. Many of the penetrations were long-term, with 19 intrusions lasting more than a year, and five lasting more than two. Targets were found in 14 different countries, across North America, Europe, India, and East Asia.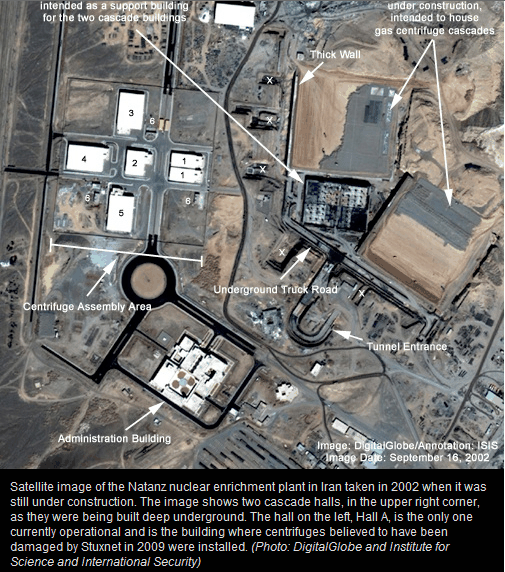 In June of 2009, someone silently unleashed a sophisticated and destructive digital worm that began slithering its way through computers in Iran with just one aim — to sabotage the country’s uranium enrichment program and prevent President Mahmoud Ahmadinejad from building a nuclear weapon.
In June of 2009, someone silently unleashed a sophisticated and destructive digital worm that began slithering its way through computers in Iran with just one aim — to sabotage the country’s uranium enrichment program and prevent President Mahmoud Ahmadinejad from building a nuclear weapon.
 Three U.S. Internet service providers are working with the National Security Agency to filter the Internet traffic flowing to 15 defense contractors in an effort to block hacker attacks, according to The Washington Post.
Three U.S. Internet service providers are working with the National Security Agency to filter the Internet traffic flowing to 15 defense contractors in an effort to block hacker attacks, according to The Washington Post.